Security
Adding PositiveSSL to a docker NGINX
Step 1: Generate the CRS
~ # openssl req -new -newkey rsa:2048 -nodes -keyout acervera.key -out acervera.csr
Can't load /root/.rnd into RNG
140292975194560:error:2406F079:random number generator:RAND_load_file:Cannot open file:../crypto/rand/randfile.c:88:Filename=/root/.rnd
Generating a RSA private key
...................................................................................................+++++
.........................................................................+++++
writing new private key to 'acervera.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:IE
State or Province Name (full name) [Some-State]:Cork
Locality Name (eg, city) []:Whitegate
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Angel Cervera Claudio
Organizational Unit Name (eg, section) []:Web
Common Name (e.g. server FQDN or YOUR name) []:www.acervera.com
Email Address []:info@acervera.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Step 2: Issue the certificate (namecheap)
- Activate Certificated Order
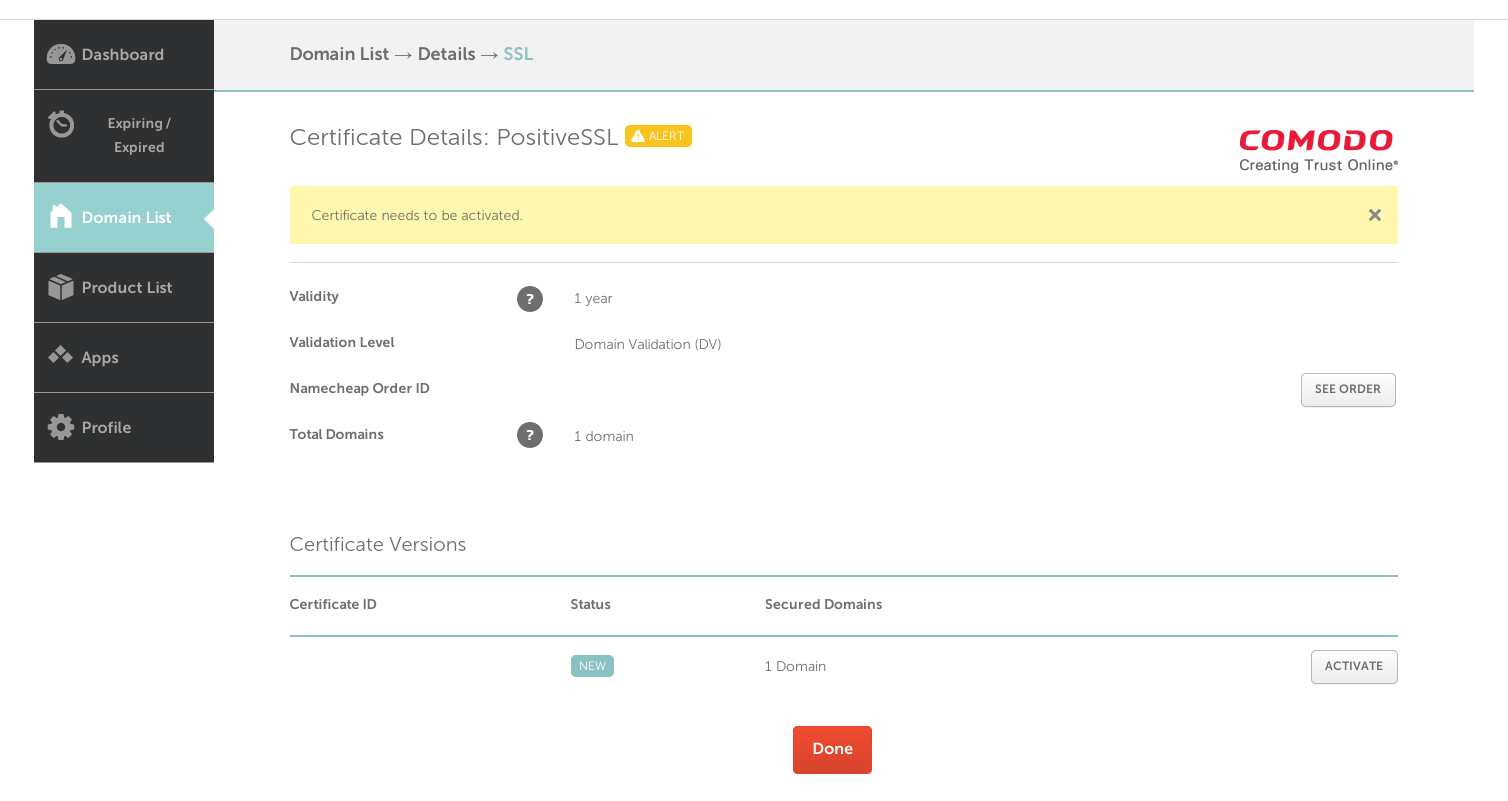
- Enter CSR and domain
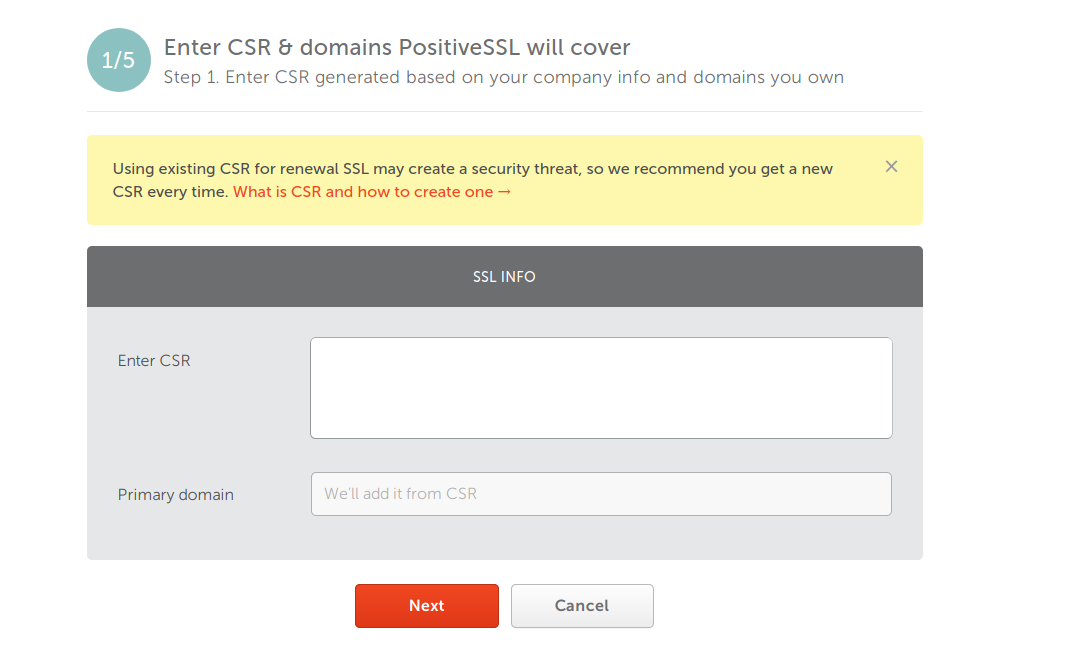
- Select type of server
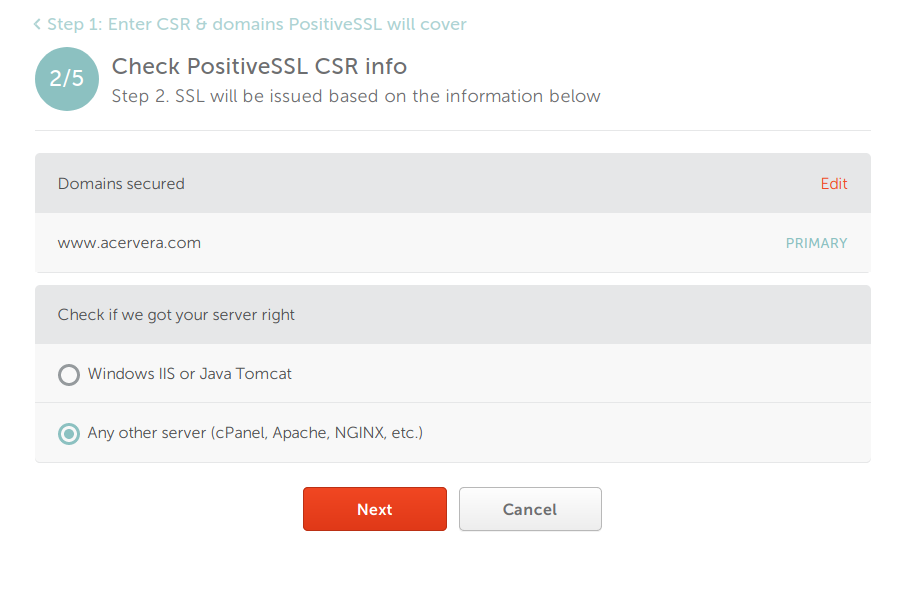
- Confirm domain owner method
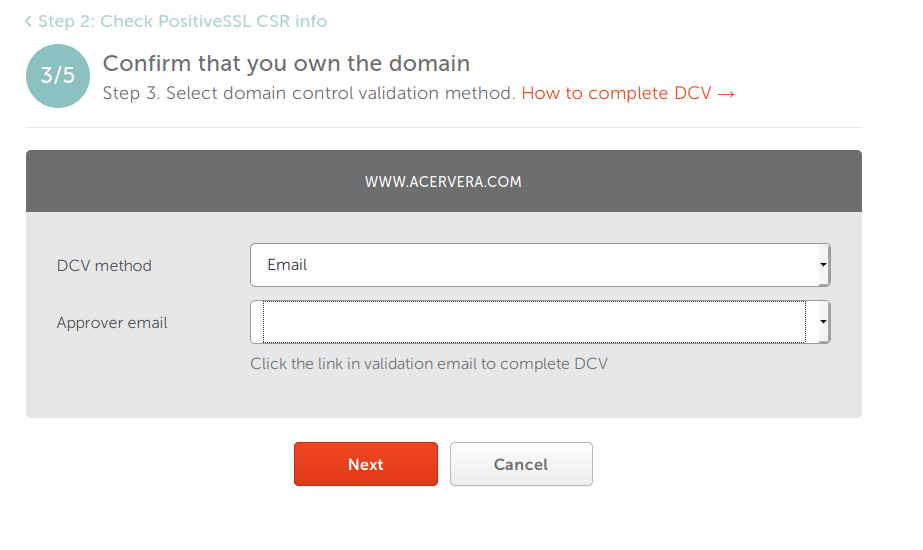
- Review and submit
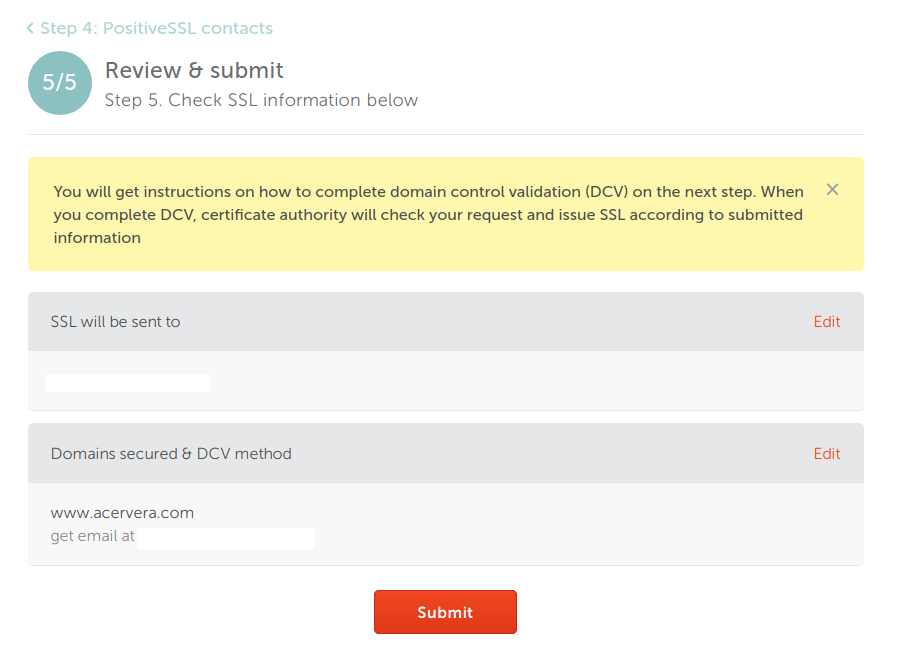
- Wait
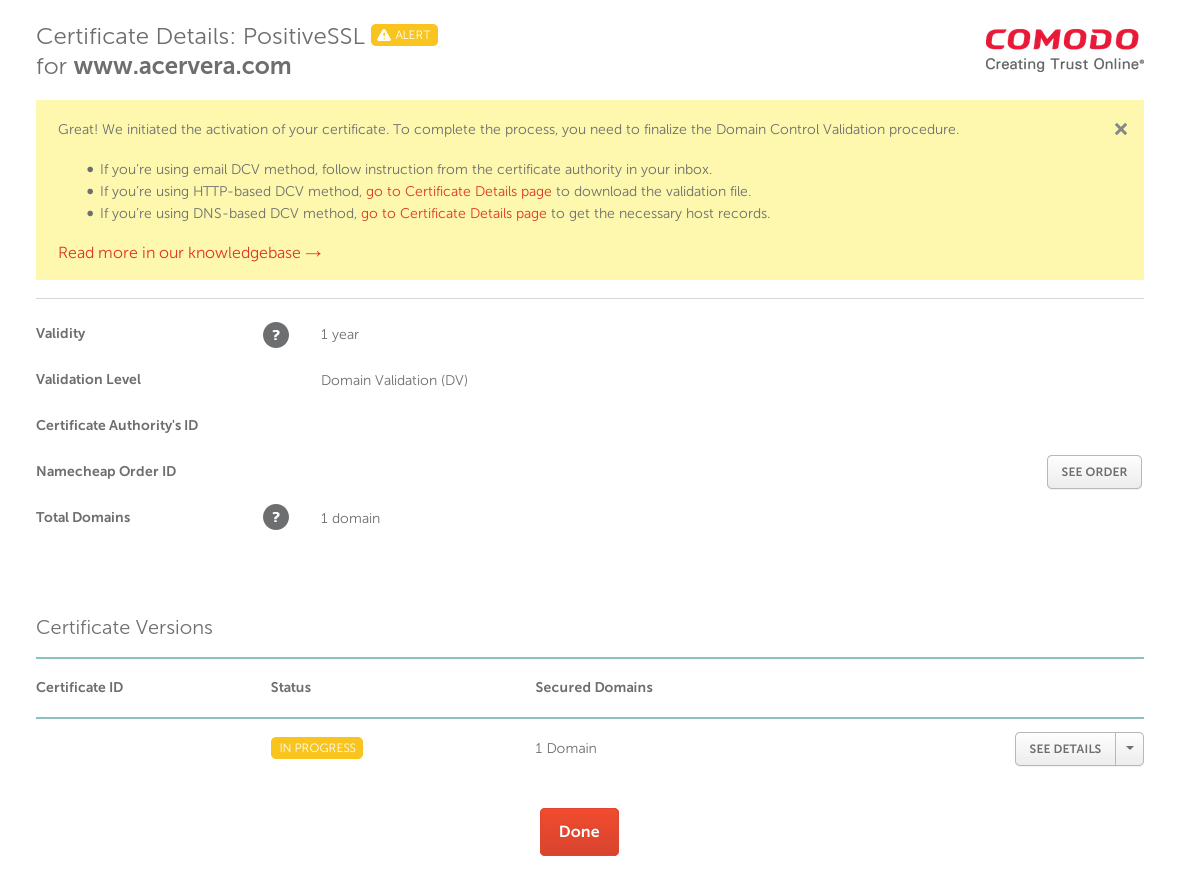
- After wait for the validation, download the certificate
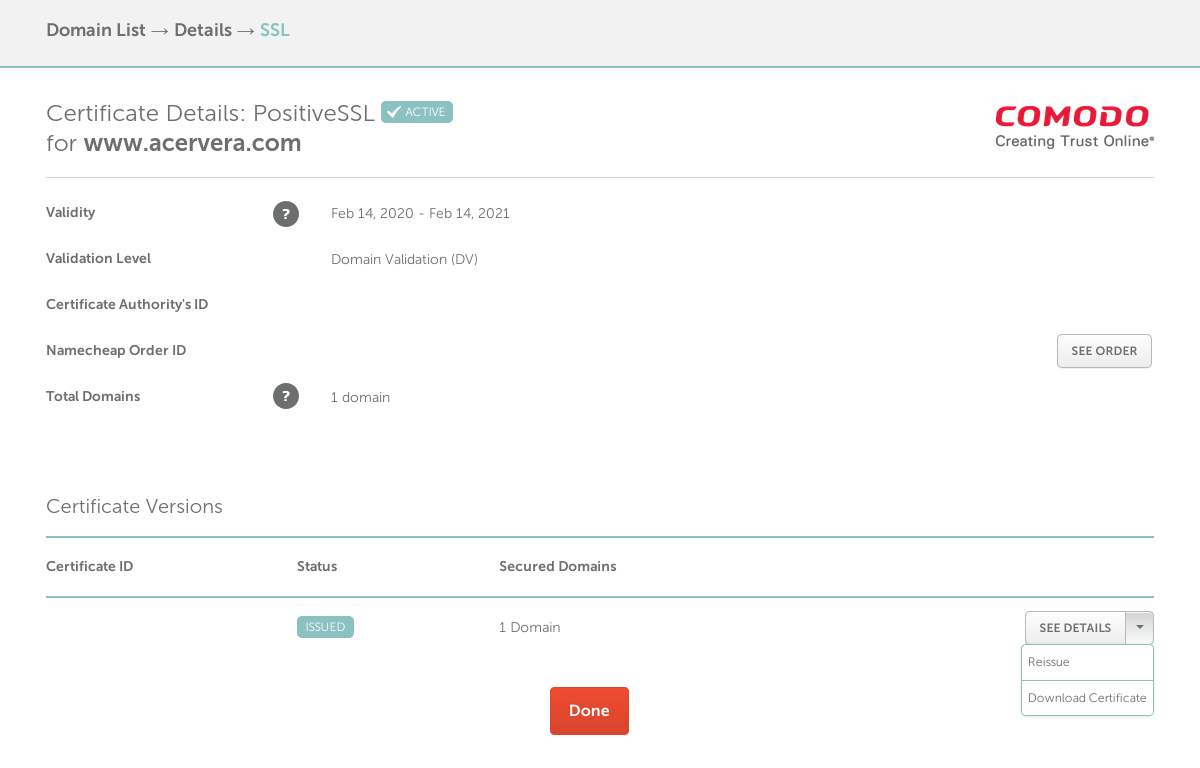
Step 3: Prepare certificate
Following the steps in the namecheap site
-
Uncompress the bundle downloaded from the previous section.
apt install unzip unzip www_acervera_com.zip -
Combine CRT and CA certificates.
cat www_acervera_com.crt www_acervera_com.ca-bundle >> www_acervera_com_chain.crtThere is a small problem with this approach.
www_acervera_com.crtdoes not contain the EOL at the end of the file, sowww_acervera_com_chain.crtis not going to have a valid format throwing the error(SSL: error:0906D066:PEM routines:PEM_read_bio:bad end line)To fix it, replace:-----END CERTIFICATE----------BEGIN CERTIFICATE-----with
-----END CERTIFICATE----- -----BEGIN CERTIFICATE----- -
Readable only be the root.
chmod 400 www_acervera_com*
Step 4. Update NGINX config
From the documentation in dockerhub The version used in my case is 1.13.12 To check it in the current running server:
# docker exec -it <container id> /bin/bash
# nginx -v
nginx version: nginx/1.13.12
Update the config file to add the SSL server
server {
listen 443 ssl http2;
ssl_certificate /etc/nginx/certs/www_acervera_com_chain.crt;
ssl_certificate_key /etc/nginx/certs/acervera.key;
server_name acervera.com *.acervera.com;
location / {
proxy_pass http://upstream-acervera;
proxy_redirect off;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Host $server_name;
}
}
server {
listen 80;
server_name acervera.com *.acervera.com;
return 301 https://$server_name$request_uri;
}
And Start docker
docker run -d \
--name nginx \
-v /root/sites/nginx.conf:/etc/nginx/nginx.conf:ro \
-v /root/sites/certs:/etc/nginx/certs \
-p 80:80 \
-p 443:443 \
nginx